- Unity User Manual 2021.2
- プラットフォーム特有の情報
- macOS
- Delivering your macOS application
- Building your macOS application
- Notarizing your macOS application
Notarizing your macOS application
Notarization is a process where Apple verifies your application to make sure it has a Developer ID code signature and doesn’t contain malicious content. For more information about noratization, see Apple’s documentation on Notarizing macOS Software Before Distribution.
If you develop on an Apple device, you can use Xcode, Xcode command-line tools, or Unity Cloud Build to notarize your application. If you don’t have an Apple device, use Unity Cloud Build.
This page contains information on the following notarization methods:
- Notarization using Xcode
- Notarization using Xcode command-line tools
- Notarization using Unity Cloud Build
Notarization using Xcode
Unity can create an Xcode project that represents your Unity project during the build process. You can use this Xcode project to notarize your application. To create an Xcode project from your Unity project, follow the macOS application build steps. For information on how to notarize the Xcode project, see Apple’s documentation on Notarizing macOS Software Before Distribution.
Notarization using Xcode command-line tools
If you are unable to notarize your application in the Xcode environment, or if you want to manually control notarization, you can use Xcode’s command-line tools. To do this, you need:
- An Apple ID.
- An Apple device that runs macOS 10.15 Catalina or later.
- Xcode 11 or later. This installs the required command-line tools.
- An Apple Developer Program membership. If you don’t have an Apple Developer membership, sign up at Apple Developer.
Code signing your application
To notarize your application with the Xcode command-line tools, you first need to code sign the application. This section explains how to code sign your application using Xcode’s command-line tools. For information about what code signing is and why Apple requires it, see Code signing.
Signing identity
Unity adds a code signature to every macOS build it produces. This is a simple code signature and doesn’t identify you as the developer. To notarize an application, Apple requires the code signature to include a cryptographic signature that identifies the developer. This is called a signing identity. Usually, you use a Developer ID certificate.
To create a new Developer ID certificate, go to Create a New Certificate:
- Follow the prompts to create a private key and upload a Certificate Signing Request.
- Download your Developer ID certificate. The file format for this certificate is
.cer. - Click on the certificate to add it to your Keychain. Within the Keychain, it appears with a name formatted like: Developer ID Application : XXX (YYY).
Application identifier
To notarize your application, Apple needs to identify it. There are two ways to get the application identifier: in Unity, or in the built application’s information property list file.
- In Unity:
- Edit > Project Settings > Player の順に移動します。
- Expand the Other Settings section and go to Mac App Store Options.
- See the value of Bundle Identifier.
- In the information property list file:
- In the Finder, go to your built application.
- Right-click on the application and select Show Package Contents.
- Go to Contents and open Info.plist.
- The key that represents the application identifier is CFBundleIdentifier.
When you have your application identifier, you can register it with Apple. To do this:
- Go to Apple Developer and log in.
- Select Certificates, IDs & Profiles.
- Select Identifiers, and add your bundle ID.
Entitlements
Entitlements are permissions or restrictions that your code signature includes that allow or prevent your application from taking specific actions. For more information, see Entitlements.
To set entitlements for your application:
- In the same directory as your built application, create a file with the same name as your application with the
.entitlementsfile extension. For example, if your application is called Sample, create a file calledSample.entitlements. - Open the file with a text editor and copy in the following content:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>com.apple.security.cs.disable-library-validation</key>
<true/>
<key>com.apple.security.cs.disable-executable-page-protection</key>
<true/>
</dict>
</plist>
These entitlements are the minimum entitlements a macOS application requires to have a Hardened Runtime. If your application requires any more entitlements, add them to this list.
Code signing
The code signing process uses the command line. To start, open Terminal and navigate to the directory that the application is in. To ensure that you have the necessary read permissions to process code signing, run the following command where "application_name.app" is the name of your application:
chmod -R a+xr "application_name.app"
A code signature uses a particular signing identity. Usually, this is your Developer ID Application signing identity. However, some digital distribution services, such as the Mac App Store require a different signing identity. For information about which signing identity a particular digital distribution service requires, see the documentation for that digital distribution service.
To code sign your application, run the following command where:
-
"application_name.app"is your built application. - `“application_name.entitlements” is the name of the entitlements file.
-
"Developer ID Application : XXX (YYY)"is your signing identity.
codesign --deep --force --verify --verbose --timestamp --options runtime --entitlements "application_name.entitlements" --sign "Developer ID Application : XXX (YYY)" "application_name.app"
This command recursively navigates through the application bundle folder, signs all files, adds a secure timestamp, and embeds the entitlements you’ve set into the signature.
Warning: Using the --deep option might cause issues with your code signature. This is because:
It applies the same code signing options and entitlements to all the code that it signs.
It only signs code files that it finds. If there are code files in a place where the system expects to find data, using
--deepdoesn’t sign these code files.
For more information about the --deep option and how to resolve issues with it, see Sign your code.
Uploading to Apple for notarization
After you code sign your application, you need to upload it to Apple for notarization. To do this, Apple requires:
- An Apple ID.
- That you compress the application.
- An application password.
- A provider short name.
Compressing the application
Apple requires that you compress your application before you upload it for notarization. To do this:
Open Terminal and navigate to the directory the application is in.
- Run the following command where:
-
"application_name.app"is your built application. -
"application_name.zip"is the name of the compressed file to generate.
-
ditto -c -k --sequesterRsrc --keepParent "application_name.app" "application_name.zip"
This compresses your application and outputs the compressed file to the same directory as your application.
Generating an application Password
To notarize an application, Apple requires a unique password in a particular format. To generate an application password, you need to have an Apple ID. If you don’t have one, go to Manage your Apple ID and create one.
For information on how to generate an application password, see How to generate an app-specific password. The password you generate uses the following format: xxxx-xxxx-xxxx-xxxx.
Getting your provider short name
A provider short name is a single-word label that identifies an individual or a company. Apple uses a provider short name to determine which organization to notarize for when your Apple ID is associated with more than one organization. To get your provider short name:
- Open Terminal.
- Run the following Xcode command where:
-
apple_idis your Apple ID. -
xxxx-xxxx-xxxx-xxxxis your application password.
-
xcrun iTMSTransporter -m provider -u apple_id -p xxxx-xxxx-xxxx-xxxx
Starting the upload process
For Apple to notarize your application, you need to upload it to their notarization servers. To do this:
- Open Terminal and navigate to the directory the compressed application is in.
- Run the following command where:
-
apple_idis your Apple ID. -
xxxx-xxxx-xxxx-xxxxis your application password. -
provider_short_nameis your provider short name. -
application_bundle_idis the application’s application identifier. -
application_name.zipis the compressed application.
-
xcrun altool --notarize-app --username apple_id --password xxxx-xxxx-xxxx-xxxx --asc-provider provider_short_name --primary-bundle-id application_bundle_id --file application_name.zip
If the upload is successful, Apple displays a response in Terminal that contains a request ID. You can use this request ID to check on the status of your request. This is useful because the notarization process might take multiple hours depending on the traffic to the service. To do this:
- Open Terminal and navigate to the directory the compressed application is in.
- Run the following command where:
-
request_idis the request ID that Apple returns from the previous command. -
apple_idis your Apple ID. -
xxxx-xxxx-xxxx-xxxxis your application password. -
provider_short_nameis your provider short name.
-
xcrun altool --notarization-info request_id --username apple_id --password xxxx-xxxx-xxxx-xxxx --asc-provider provider_short_name
When the notarization process is complete, Apple sends you a confirmation email at the address associated with your Apple ID. You can then verify that notarization was successful. To do this:
- Open Terminal and navigate to the directory the application is in.
- Run the following command where:
-
application_name.appis the name of your application:
-
spctl -a -v application_name.app
If notarization was successful, this returns a message that indicates that Apple accepted the application and includes your Developer ID.
Stapling the application
After notarizing your application, any device that runs it can verify that it has a code signature and contains no malicious content. However, the device can only perform this verification if it has an internet connection. To make a device able to verify your application without an internet connection, you must staple the application. For information about stapling, see Staple the Ticket to Your Distribution. To staple your application,
- Open Terminal and navigate to the directory the application is in.
- Run the following command
"ApplicationName.app"is the name of your application:xcrun stapler staple "ApplicationName.app".
Notarization using Unity Cloud Build
Unity Cloud Build can notarize and staple your macOS application during the build process. To do this, Unity requires:
- An Apple ID.
- An application-specific password.
- An Apple Developer Program membership.
- An entitlements file.
- A Developer ID certificate exported in the PKCS #12 Personal Information Exchange (.p12) file format.
- The password you used to create the
.p12file. - Your provider short name.
Depending on the platform you are developing on, the process for some of these requirements differ. If you develop on an Apple device, you can use Xcode command-line tools to get the information and create the relevant files. However, If you develop on Windows or Linux, you don’t have access to Apple-specific Xcode command-line tools.
Regardless of which platform you use, the process to get the Apple ID, password, and entitlements files are platform-agnostic:
- If you don’t have an Apple ID, go to Manage your Apple ID and create one.
- Create an application password. For information on how to do this, see Generating an application Password.
- If you don’t have an Apple Developer membership, sign up at Apple Developer.
- Create an entitlements file for your application. For information on how to do this, see Entitlements.
After you complete these steps:
- If you are developing on macOS, see Unity Cloud Build notarization for Apple devices.
- If you are developing on Windows or Linux, see Unity Cloud Build notarization for Windows and Linux devices.
Unity Cloud Build notarization for Apple devices
If you develop on an Apple device, you can use Xcode command-line tools to meet the requirements listed in Notarization using Unity Cloud Build. You can then set up Unity Cloud Build to notarize and staple your application as part of the build process. To meet the requirements:
- Follow the platform-agnostic steps in Notarization using Unity Cloud Build.
- Create a Developer ID certificate and add it to your Keychain. For information on how to do this, see Signing identity.
- From the Keychain, export the Developer ID certificate as a file in Personal Information Exchange (
.p12) format. For information on how to do this, see Import and export keychain items using Keychain Access on Mac. - Get your provider short name. For information on how to do this, see Getting your provider short name.
After you meet the requirements, fill out and submit the Unity Cloud Build notarization form.
Unity Cloud Build notarization for Windows and Linux devices
If you develop on Windows or Linux but want to build, notarize, and staple your application for macOS, you can’t use Xcode command-line tools. To meet the requirements listed in Notarization using Unity Cloud Build so you can set up Unity Cloud Build to notarize and staple your application as part of the build process:
- Follow the platform-agnostic steps in Notarization using Unity Cloud Build.
- Create a Developer ID certificate and download it. For information on how to do this, see Signing identity. Note: The last step in Signing identity is only relevant for macOS users.
- Convert the Developer ID certificate to the PKCS #12 Personal Information Exchange (.p12) file format. For information on how to do this, see Converting a Developer ID certificate to a .p12 file on Windows and Linux.
- Get your provider short name through your Apple Developer account. To do this, go to Membership Details and find your Team ID. You can use the Team ID as a provider short name.
After you meet the requirements, fill out and submit the Unity Cloud Build notarization form.
Converting a Developer ID certificate to a .p12 file on Windows and Linux
A .p12 file bundles both your Developer ID certificate and a private key. To create one from your Developer ID certificate:
Open a command-line interface and go to the directory that contains your Developer ID certificate file. If you didn’t download your Developer ID certificate, see Signing identity.
- Developer ID certificates use the
.cerfile format. Convert this file to the.pemfile format. To do this, run the following command where:-
developer_identity.ceris the Developer ID certificate file to convert. -
developer_identity.pemis the file name and file type to output.
openssl x509 -in developer_identity.cer -inform DER -out developer_identity.pem -outform PEM -
- Generate a new private key. To do this, run the following command where:
-
mykey.keyis the file name and file type of the private key to output.
openssl genrsa -out mykey.key 2048 -
- Generate the
.p12file. To do this, run the following command where:-
mykey.keyis the private key file you generated in step 3. -
developer_identity.pemis the.pemfile you generated in step 2.
openssl pkcs12 -export -inkey mykey.key -in developer_identity.pem -out iphone_dev.p12 -
Submitting the Unity Cloud Build notarization form
After you meet the requirements outlined in Notarization using Unity Cloud Build, follow these steps to setup Unity Cloud Build notarization:
- Set up your project to use Unity Cloud Build. For information on how to do this, see Unity Cloud Build.
- Create a new Mac Desktop build target in Cloud Build.
- Return to the Config page. This page now includes the Notarization section. Open this section and click EDIT NOTARIZATION.
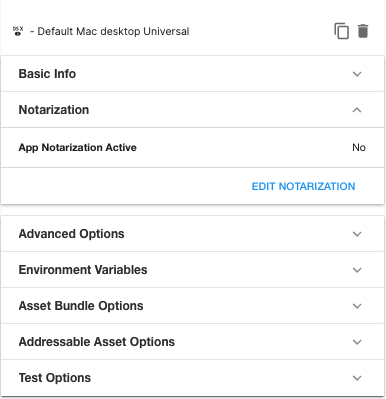
- Enable the Notarization flag. If you have previously supplied a set of notarization credentials to Unity Cloud Build, for the same Organization, you can select those from Credentials. Otherwise, select Add new provisioning credentials.
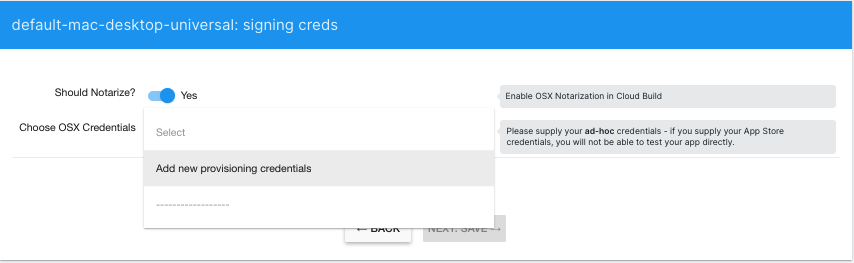
- Provide the following:
- Name: the name for your credentials set. You can use these credentials for any additional projects you set up in the same organization.
-
p12 File: The
.p12file you created in either Unity Cloud Build notarization for Apple devices or Unity Cloud Build notarization for Windows and Linux devices, depending on your platform. - Entitlements File (optional): The entitlements file you created in Notarization using Unity Cloud Build. If you do not provide an entitlements file, Unity Cloud Build uses the minimum entitlements a macOS application requires to have a Hardened Runtime. For information on what these minimum entitlements are, see Entitlements.
-
p12 Password: The password you supplied when you created the
.p12file. - Provider Short Name (optional): The provider short name you acquired in either Unity Cloud Build notarization for Apple devices or Unity Cloud Build notarization for Windows and Linux devices, depending on your platform. If your Apple ID is associated with more than one organization and you don’t provide this, notarization fails.
- Apple ID Username: Your Apple ID username.
- Apple ID Password: The application password you created in Notarization using Unity Cloud Build. Unity Cloud Build does not verify Apple credentials until it attempts to notarize your build, so make sure to enter the correct username and password.
-
Confirm your Apple ID Password: A repeat of the Apple ID Password.
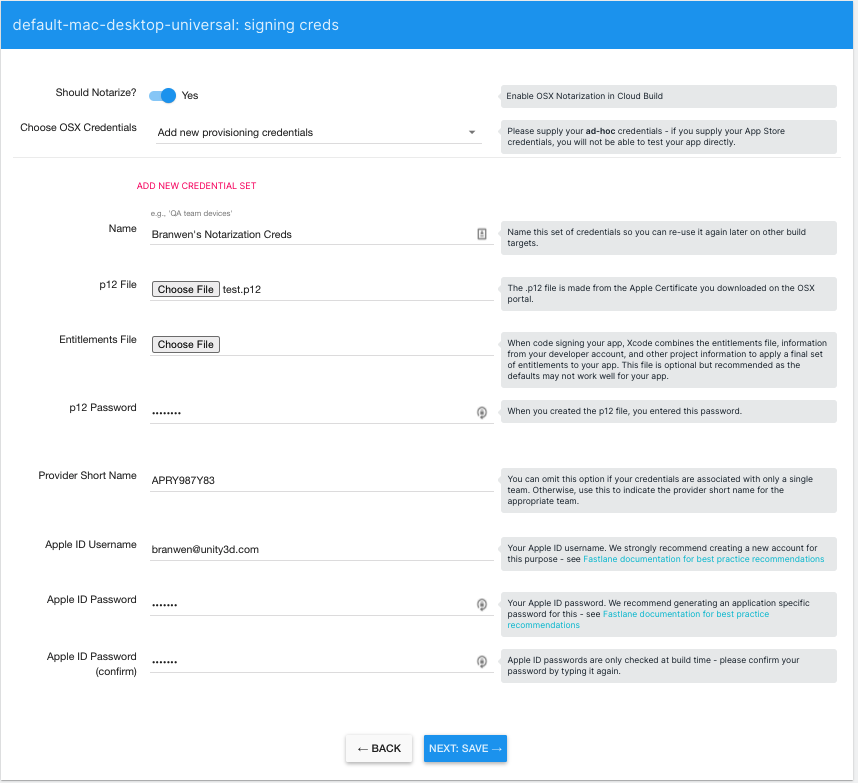
- Save your credentials.
- Return to the Build History page and start a build for your Mac target.
- If the build succeeds, Unity Cloud Build attempts to notarize and stable the result.
- Cloud Build runs the
codesigncommand with the following flags:--deep --force --verify --verbose --timestamp --options runtime. It’s not currently possible to specify custom flags. - If you want to see additional log output from notarization, set the environment variable
FASTLANE_NOTARIZE_VERBOSE=truein your build target Environment Variables.
- Cloud Build runs the
- After Unity Cloud Build builds, notarizes, and staples your project, you can download a compressed file that contains the build.